Cybercrime increases amid COVID-19
A global pandemic, record unemployment and college campuses shifting to virtual classrooms have created the “perfect storm” for cybercrime in higher education, according to Information Technology Services officials.
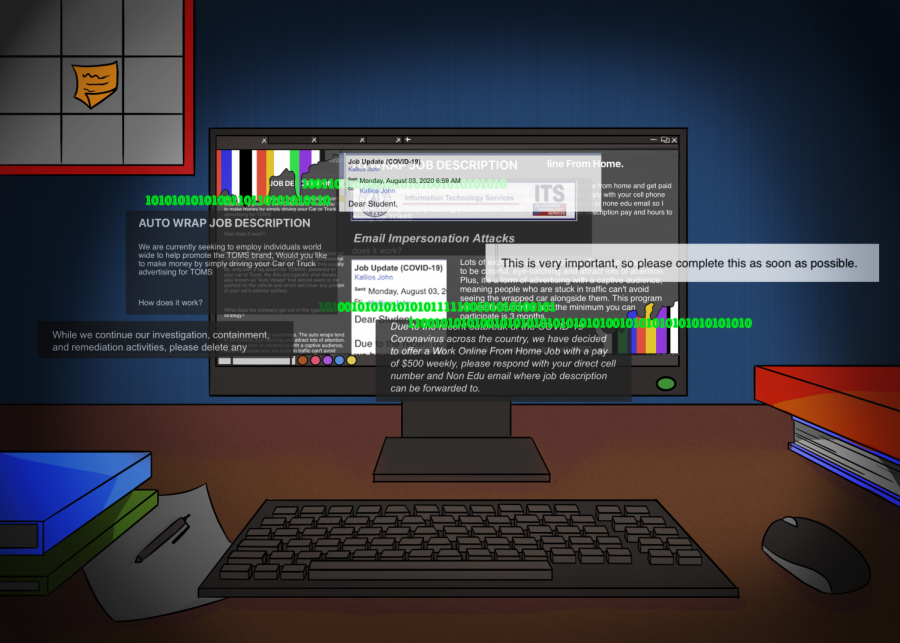
An email sent out on April 10 by Student Information Services said the COVID-19 pandemic has increased cybercrime and phishing attacks by around 670%.
After campus shut-downs began, El Camino’s IT Services had to process requests for remote access for all the endpoints. That meant every device on and off campus, used by every student, faculty and staff members at El Camino College could be a potential breach-point for cybercriminals.
According to the Department of Justice, the Secret Service, and World Health Organization, cybercriminals have been using COVID-19 as a tool for worldwide exploitation.
“Cybercriminals, in general, take advantage of crises,” Loic Audusseau, El Camino College’s Chief Technology Officer, said.
Audusseau heads up all IT operations and strategic initiatives on campus.
“The whole pandemic changed dramatically how we operate, specifically when it comes to technology,” Audusseau said.
Audusseau was hired by El Camino College as Chief Technology Officer in July to acclimate him in his position ahead of students returning to virtual classes this fall.
The “attack surface” before Covid-19 was limited to networks and internal resources. Any endpoints (computers and devices) that could be a potential point of attack were limited to the computers and network on campus, according to Audusseau.
Cybercriminals have been targeting ECC students with “fake job and hiring scam” emails via a compromised elcamino.edu account, according to a campus-wide notification on August 5.
Paul Yoder, the Information Security Specialist in charge of cyber security at ECC, said that attacks like these “have been going on forever.”
Yoder added that there are three types of typical attacks: Drive-By-Malware, where clicking a link secretly downloads a payload or malware to the system; Pure Phishing, where people are asked to share Personal Identifiable Information (PII); and Spear Phishing, which specifically targets gate-keepers like secretaries, assistants and employees that routinely run errands for superiors, asking them to purchase gift cards with the promise to reimburse them later.
“This is social engineering at it’s finest,” Yoder said.
Nicole Fayaz, a risk management consultant for community colleges and K-12 school districts in California said that cybercriminals are getting smarter everyday and schools need to stay ahead of the game instead of playing catch up “because it’s not if, but when.”
Audusseau and Yoder say there are 3 simple tips that students, faculty and staff members can use to better protect themselves.
First, practice good “cyber hygiene.” Cybercriminals most often get access to .edu email accounts when people use them and the same password to create other accounts on external sites like Instacart and Facebook.
Secondly, beware of all emails in your ECC email inbox marked [EXTERNAL]. Especially ones that have job offers, ask for personal identifiable information, promise to send cashiers checks or emails, that look like they’re from a boss, asking people to purchase gift cards or gift vouchers.
Lastly, Audusseau and Yoder remind staff, students and faculty members the age-old adage that “if an offer seems too good to be true, it probably is.”
EDITOR’S NOTE: THIS STORY WAS UPDATED OCT. 16 AND AGAIN ON OCT. 26 TO CORRECT A MISSPELLING.
LINK TO A WORLD HEALTH ORGANIZATION ARTICLE WAS REMOVED ON DEC. 10 AT 8:14 P.M. AS THE LINK IS NO LONGER LIVE.